- Already have a cluster up and running as described in Getting cockroachDB running with Kubernetes and are using the Google Cloud console shell with the kubectl CLI. The database is of course not necessary for this example, but the cluster and CLI preparation is.
- created an app to be deployed as described in Building your App ready for Kubernetes deployment
- deployed it as described in Creating a Kubernetes deployment
- created a service as described in Creating a microservice on Kubernetes
- created an ingress controller as described in Bringing up an ingress controller
- started the cert-manager process described in Managing ssl for ingress certificates with cert-manager
- added an A record to the DNS record for the domain you’ll be assigning your app pointing at the ip address exposed by Bringing up an ingress controller
- You might also find Digging around on the Kubernetes cluster of some use to help with the familiarity of concepts.
I recommend that you save your commands in various scripts so you can repeat them or modify them later.
In this article – we’re doing this.
Page Content
hide
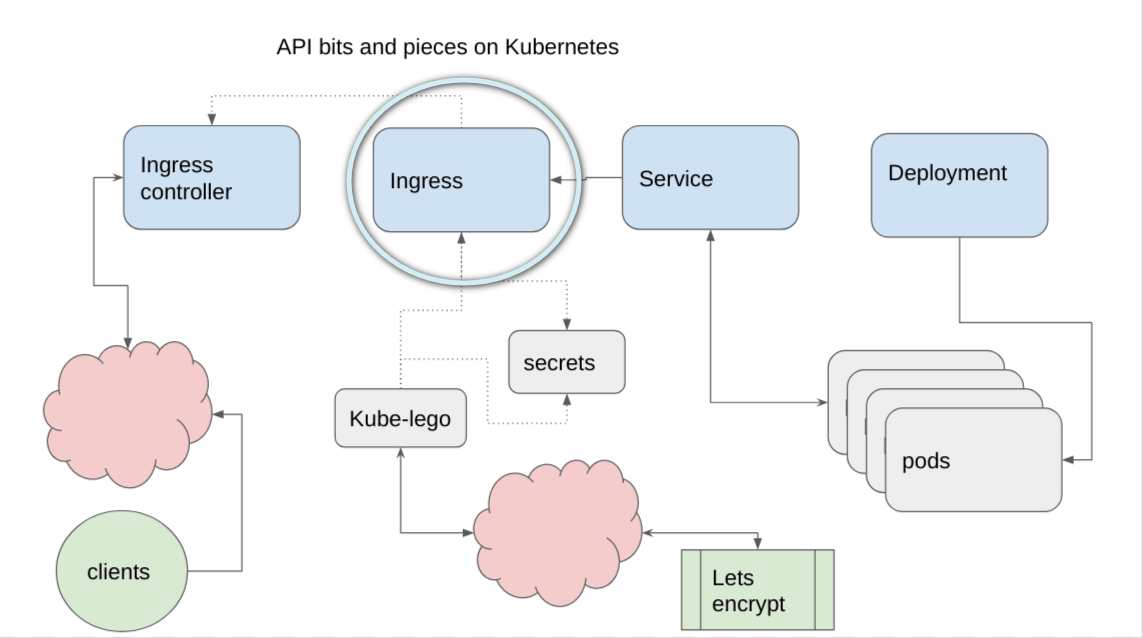
Ingress
This is the last step to getting your app out there. For my example, I’m using one of my existing domains, and services so I won’t go into the app itself here. For an example app you can see Getting a simple app running on Kubernetes
make-ingress.yaml
apiVersion: extensions/v1beta1
kind: Ingress
metadata:
name: fidkp-ingress
annotations:
ingress.kubernetes.io/ssl-redirect: "true"
kubernetes.io/tls-acme: "true"
kubernetes.io/ingress.class: "nginx"
certmanager.k8s.io/cluster-issuer: "letsencrypt-prod"
spec:
tls:
- hosts:
- xxx.xxx.yourdomain.con
secretName: api-fid-prod-crt
rules:
- host: xxx.xxx.yourdomain.com
http:
paths:
- path: /
backend:
serviceName: fidkp-service
servicePort: 80
- The annotations tell the ingress how to get its tls secret created by the cert-manager clusterissuers described in Managing ssl for ingress certificates with cert-manager, and associates it with an ingress controller created in Bringing up an ingress controller
- The service associates it with the service name of the type described in Creating a microservice on Kubernetes
and you can apply it
make-ingress.sh
kubectl apply -f make-ingress.yaml
Next step
We’re done – thanks for sticking with me the whole way.